Every business today faces a significant risk from network vulnerabilities, which can lead to substantial financial and reputational damage.
A data breach can cost a company an average of $4.45 million in lost business, underscoring the severe impact these incidents can have on an organization’s bottom line.
At the heart of this threat are network security vulnerabilities, which serve as gateways for cyber attackers to exploit and harm an organization’s digital infrastructure.
| As Jason Cary, VP of Sales at FTI Services says, “Vigilance in network security is the key to fortifying digital defenses.” |
Understanding the types of vulnerabilities in network security is crucial for developing robust defenses against these threats.
Common Network Vulnerabilities to Look Out for
1. Software Flaws
Software flaws, including outdated software and unpatched vulnerabilities, stand as common network vulnerabilities. Cyber attackers exploit these weaknesses to infiltrate networks, steal data, and cause disruptions. Regular updates and vulnerability scanning are essential to mitigate these risks.
2. Weak Passwords
Weak passwords are a primary security risk, making it easy for malicious actors to gain unauthorized access. In fact, 3 in 10 users have been victims of data breaches due to weak passwords. Strong password policies and encouraging complex, unique passwords can significantly enhance network security.
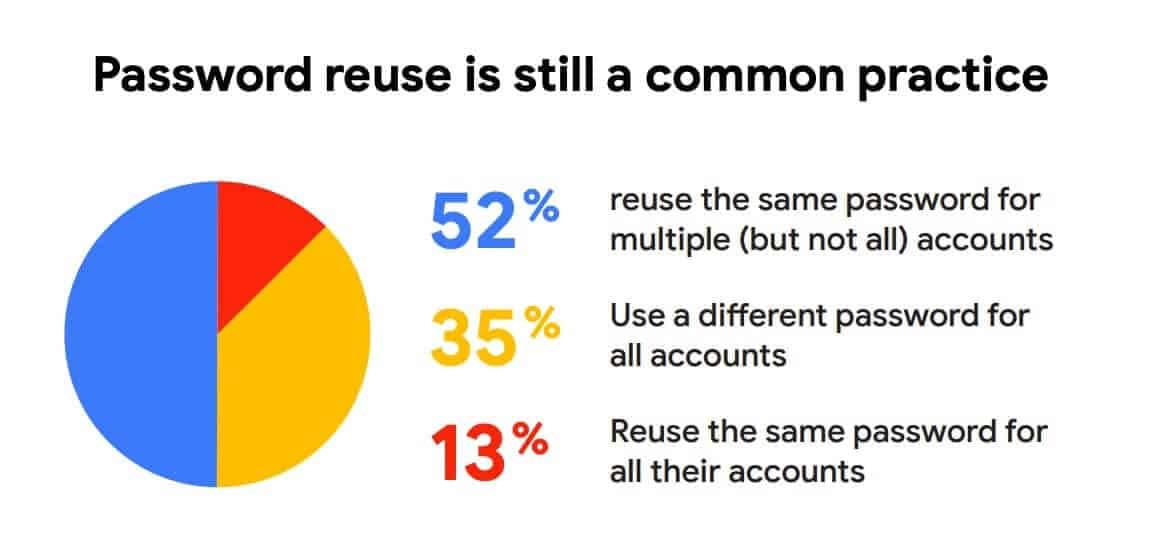
Source: Comparitech
3. Social Engineering Attacks
Social engineering attacks, such as phishing, manipulate individuals into disclosing sensitive information. Educating employees about these cyber threats and vulnerabilities can help prevent data breaches.
4. Misconfigured Network Devices
Improperly configured routers, switches, and firewalls can introduce severe network security vulnerabilities. Regular audits and adherence to best practices in configuring network devices are crucial to safeguard against these attacks on network security.
5. Insider Threats
Did you know that insider threats cause 60% of data breaches? Insider threats, whether intentional or accidental, pose a significant security challenge. Implementing strict access controls and monitoring user activities can help mitigate these information security vulnerabilities.
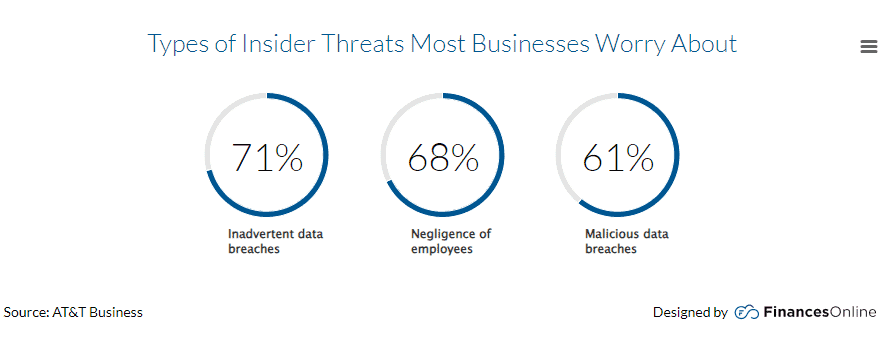
Source: FinancesOnline
6. Zero-day Exploits
Zero-day exploits target unknown or unpatched vulnerabilities. Staying ahead of these cyber vulnerabilities requires a comprehensive security strategy that includes regular updates, penetration tests, and threat intelligence.
7. Outdated Operating Systems
Operating systems that are no longer supported and receive no security updates, making them vulnerable to cyber attackers. Ensuring all systems run on supported versions with the latest security patches is a vital security measure.
8. Man-in-the-Middle (MitM) Attacks
Man-in-the-Middle (MitM) attacks occur when a cyber attacker intercepts communication between two parties to steal or manipulate the data being exchanged. This vulnerability exploits insecure or unencrypted network connections, making it vital for organizations to implement secure communication protocols like HTTPS and use VPNs for data transmission.
9. Distributed Denial of Service (DDoS) Attacks
DDoS attacks overwhelm network resources, rendering services unavailable. Protection against these types of network security threats involves robust infrastructure and proactive monitoring to detect and mitigate attacks.
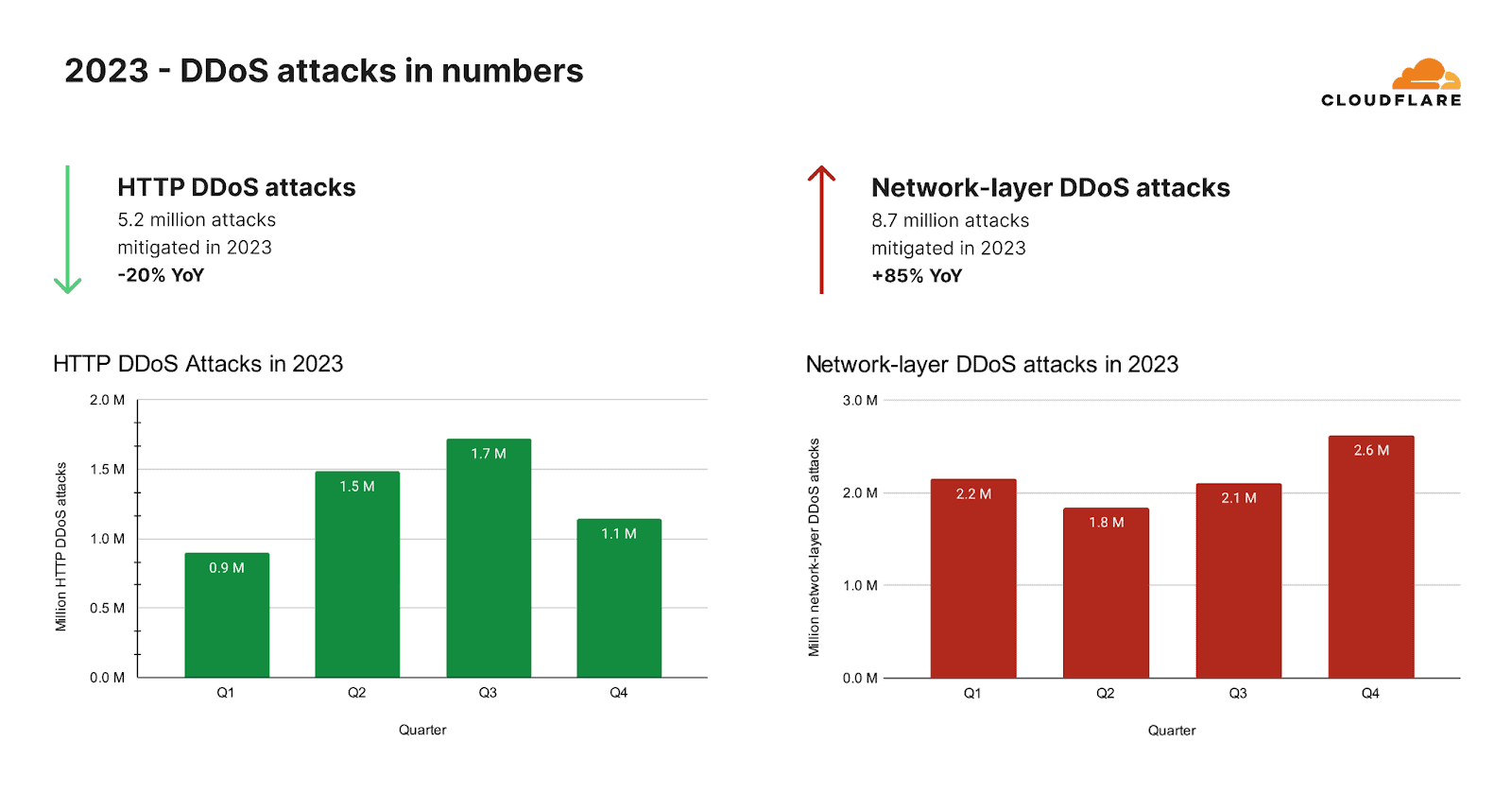
Source: Cloudfare
10. IoT Vulnerabilities
The increasing use of Internet of Things (IoT) devices in businesses introduces new network security vulnerabilities. These devices often lack robust security features, making them easy targets for cyber attackers to exploit and gain access to wider network systems.
Ensuring that all IoT devices are securely configured and regularly updated, along with segmenting them from critical network areas, can help mitigate these risks.
| More resources you might like: |
Comparative Overview of Essential Network Security Measures
| Security Measure | Function | Benefit |
| Firewalls | Blocks unauthorized access to networks | Enhances network perimeter security |
| Antivirus Software | Detects and removes malware | Protects against viruses, spyware |
| Intrusion Detection Systems (IDS) | Monitors network traffic for suspicious activity | Early detection of cyber threats |
| Intrusion Prevention Systems (IPS) | Blocks potentially harmful traffic | Actively prevents attack attempts |
| Virtual Private Networks (VPNs) | Encrypts internet traffic | Secures remote access and data transmission |
Safeguard Your Business Against Network Vulnerabilities with FTI Services
In today’s digital age, understanding and addressing network vulnerabilities is more important than ever. Businesses of all sizes must stay informed about potential security risks and take necessary precautions to protect their information.
While the specifics of network security can be complex, the fundamental goal remains clear: to safeguard data and maintain the integrity of digital infrastructure.
| Explore our range of IT services in Ventura:
|
By staying vigilant and adopting basic security measures, organizations can make significant strides in preventing cyber threats. For those seeking additional support, consulting with cybersecurity experts like FTI Services can provide further guidance and peace of mind.
Reach out to us for a free consultation and take a decisive step towards securing your digital assets against the evolving landscape of cyber risks.


